1. Dependency Security
Why dependency security matters
-
A single vulnerable package can expose your entire application
-
Attackers target popular packages because they affect many apps
- Supply chain attacks are increasing every year
Common tools for dependency security
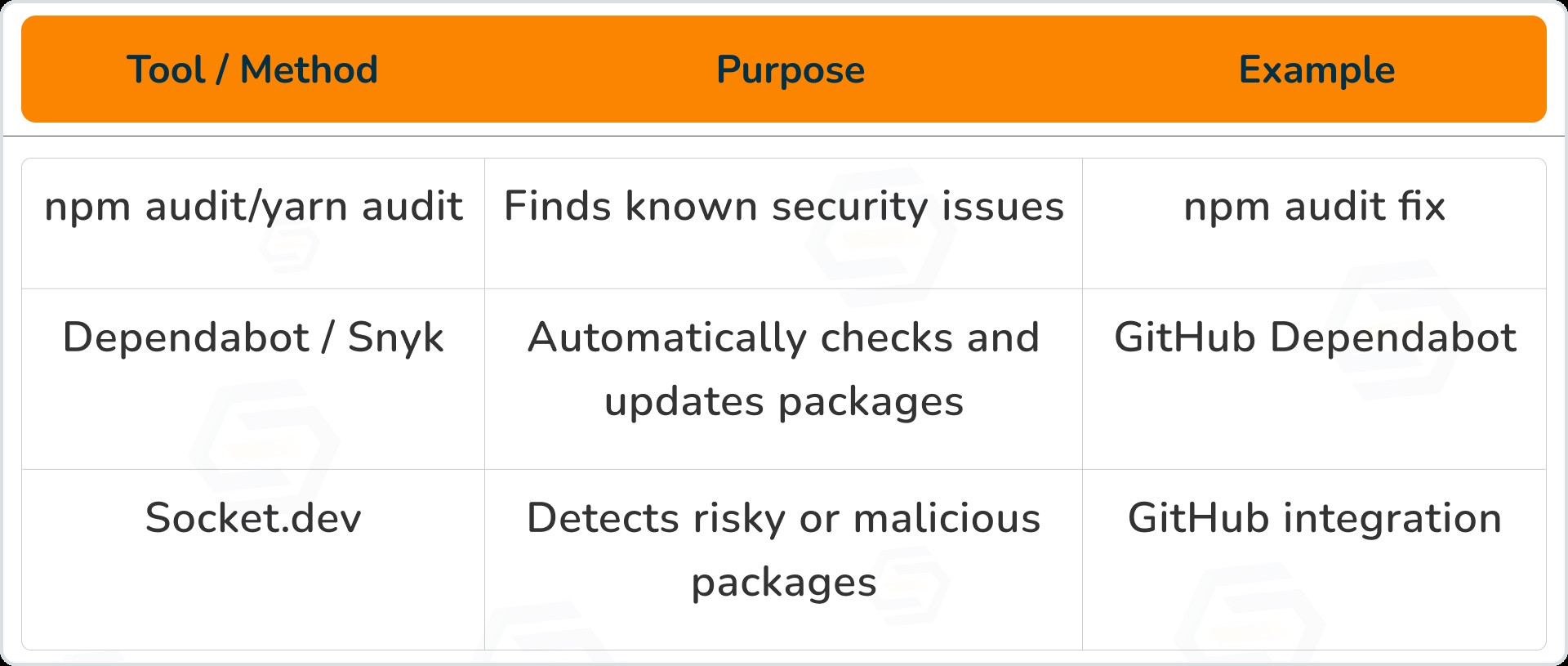
Best practice
-
package-lock.json
-
yarn.lock
Example commands
# Check for known vulnerabilities
npm audit
# Fix issues automatically
npm audit fix
2026 Supply Chain Attack Trend
Supply chain attacks are becoming one of the biggest threats to Node.js apps.
Supply Chain Attacks (2024–2026)
--------------------------------
2024: 25%
2025: 40%
2026: 55%By 2026, more than half of Node.js security incidents are expected to come from compromised dependencies. This makes regular audits and automatic updates extremely important.
2. Authentication & Authorization
Authentication methods and 2026 recommendations

Why passwords are risky
-
Users reuse passwords
-
Passwords get leaked or guessed
- Phishing attacks steal credentials easily
Why passkeys and OAuth are better
-
No shared secrets
-
Strong cryptography
- Harder to steal or reuse
Example: JWT Verification in Express
import jwt from "jsonwebtoken";
import { Request, Response, NextFunction } from "express";
export function authMiddleware(req: Request, res: Response, next: NextFunction) {
const token = req.headers["authorization"]?.split(" ")[1];
if (!token) return res.status(401).json({ error: "Unauthorized" });
try {
const decoded = jwt.verify(token, process.env.JWT_SECRET as string);
(req as any).user = decoded;
next();
} catch {
res.status(403).json({ error: "Forbidden" });
}
}This ensures:
-
Only logged-in users can access protected routes
-
Invalid or expired tokens are blocked
3. Input Validation & Sanitization
Common threats and how to prevent them

Example: Input Validation with Zod
import { z } from "zod";
const userSchema = z.object({
email: z.string().email(),
age: z.number().min(18),
});
try {
userSchema.parse({ email: "test@example.com", age: 17 });
} catch (err) {
console.error("Invalid input:", err.errors);
}This protects your app by:
-
Blocking invalid data early
-
Preventing unexpected crashes
- Reducing attack surface
4. Secret Management
-
API keys
-
Database passwords
- JWT secrets
- Cloud credentials
Best practices
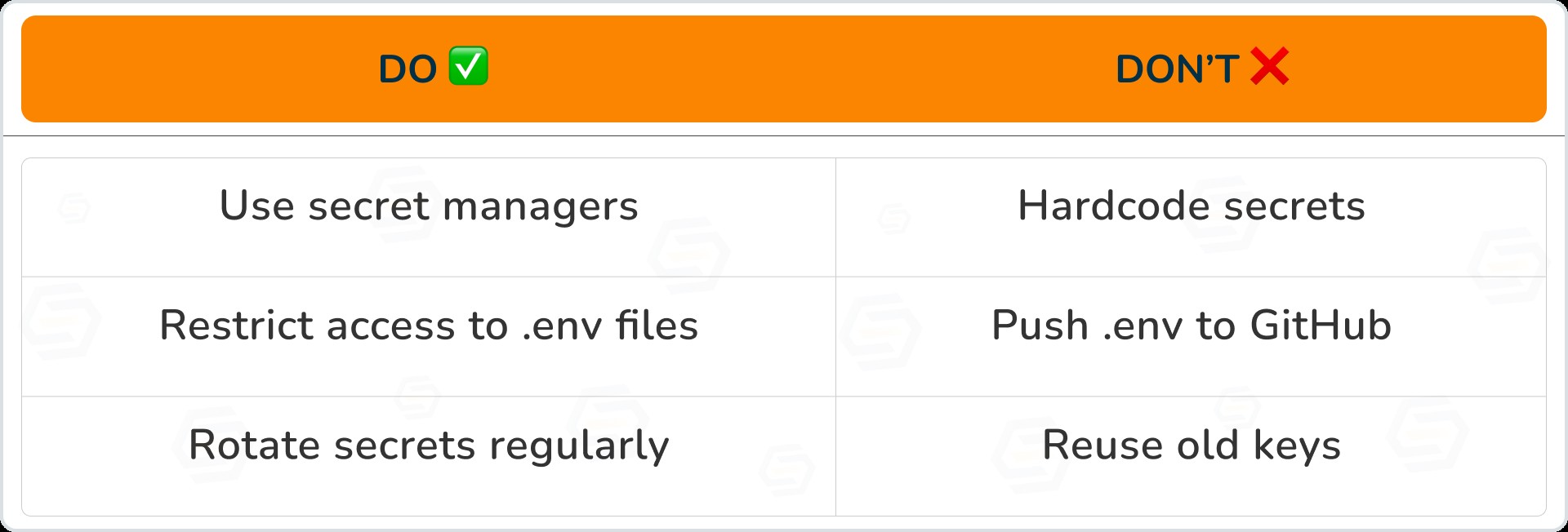
Example: AWS Secrets Manager
import AWS from "aws-sdk";
const client = new AWS.SecretsManager();
async function getSecret(secretName: string) {
const data = await client.getSecretValue({ SecretId: secretName }).promise();
return JSON.parse(data.SecretString as string);
}This keeps secrets:
-
Out of your code
-
Encrypted
- Easy to rotate
5. HTTPS, TLS & Security Headers
-
Faster connections
-
Better encryption
- Improved security
Using Helmet.js for security headers
import helmet from "helmet";
import express from "express";
const app = express();
app.use(helmet());A helmet helps protect against:
-
XSS
-
Clickjacking
- MIME sniffing
TLS Adoption Trend
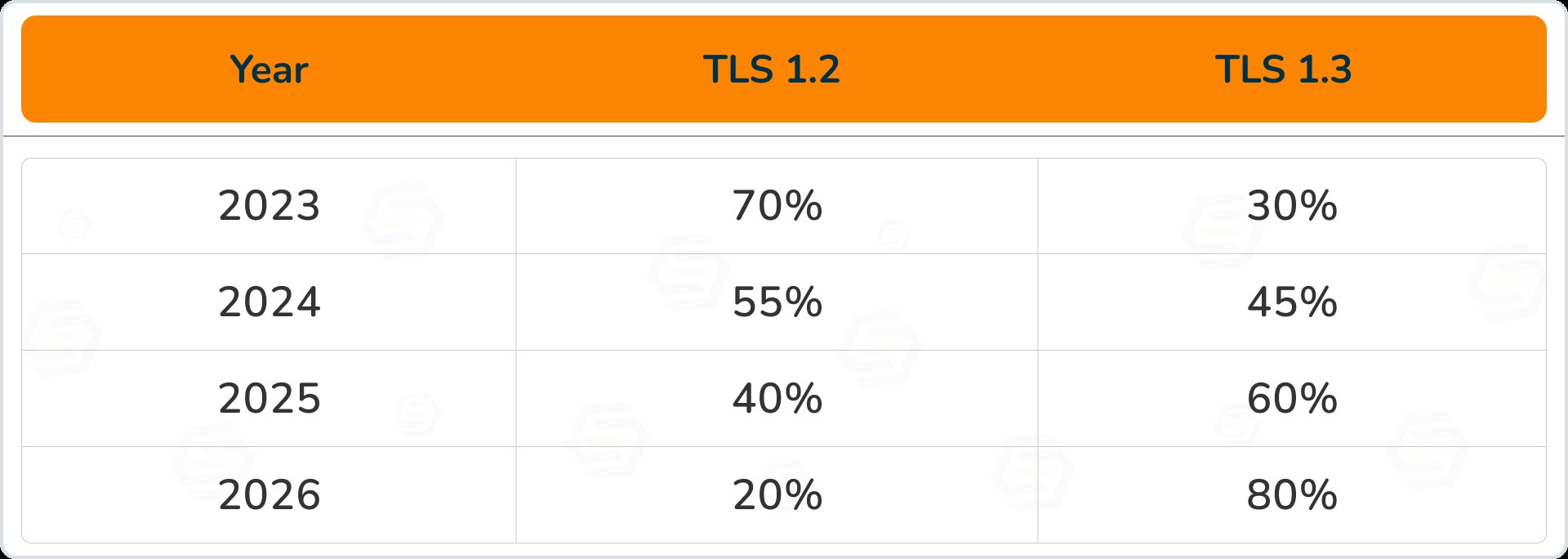
6. Rate Limiting & DDoS Protection
Express rate limiting example
import rateLimit from "express-rate-limit";
const limiter = rateLimit({
windowMs: 15 * 60 * 1000,
max: 100,
});
app.use(limiter);
Tools for protection
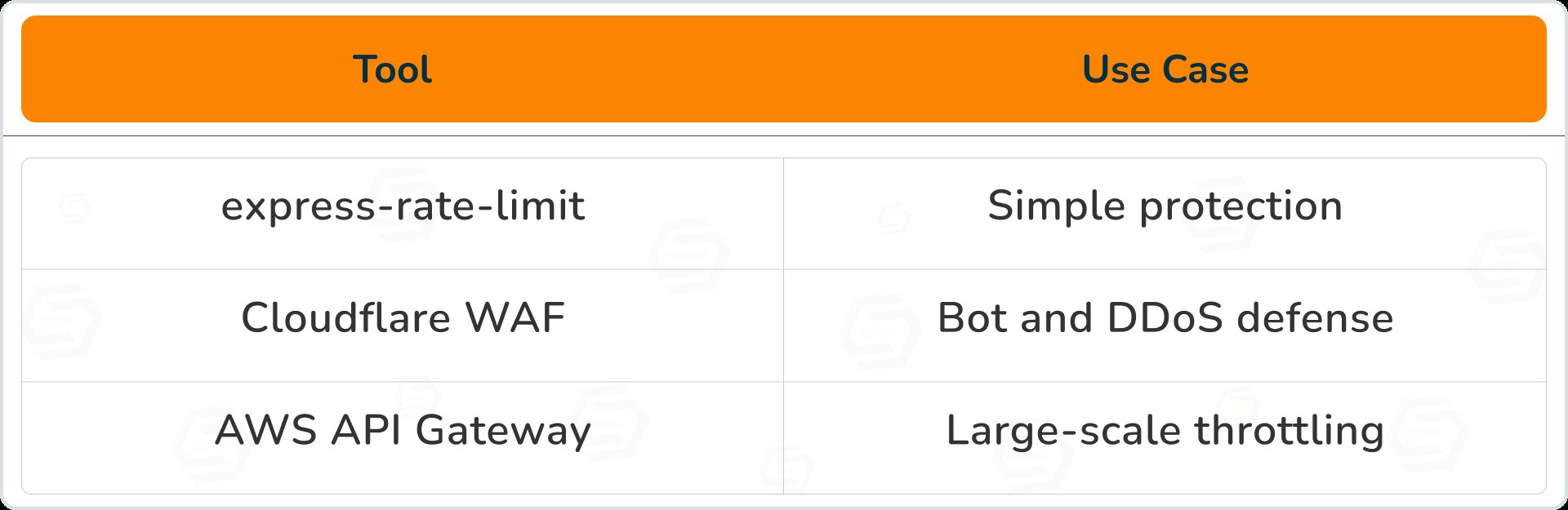
7. Container & Serverless Security
Best practices
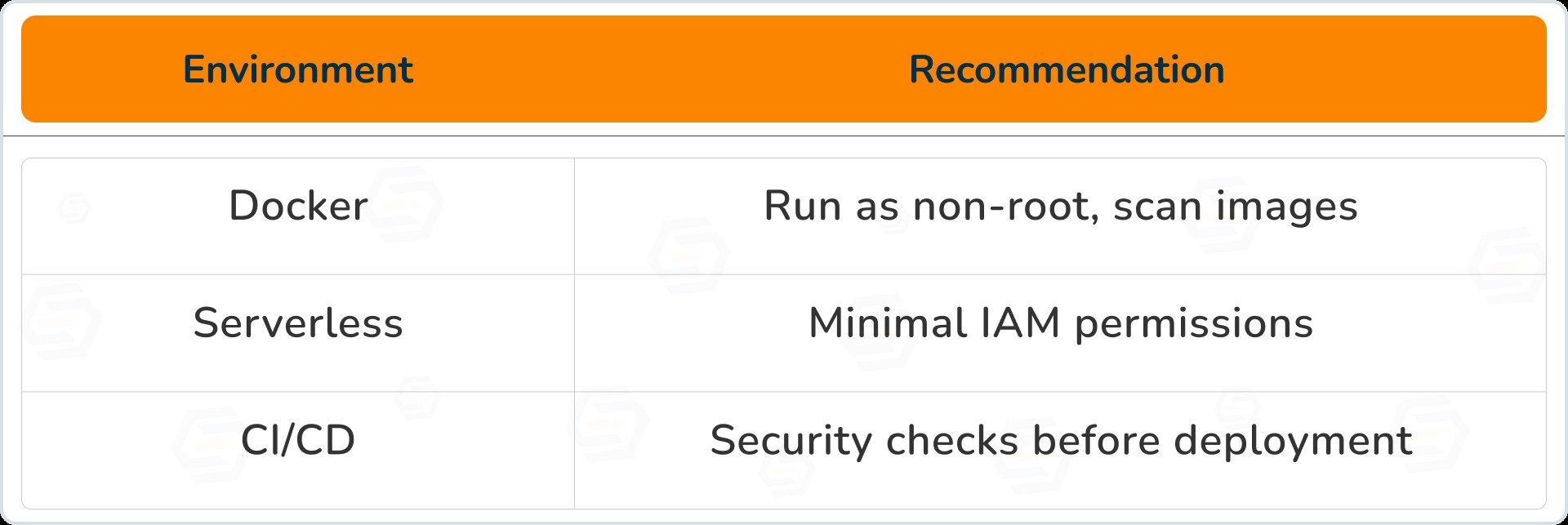
Docker scan example
trivy image node:18-alpineThis finds:
-
OS vulnerabilities
-
Package issues
- Misconfigurations
8. Monitoring & Logging
-
Detect attacks
-
Debug problems
- Meet compliance needs
Example with Pino
import pino from "pino";
const logger = pino();
logger.info("Server started");
logger.error("Something went wrong");Best practices
-
Use structured logs
-
Send logs to central tools
- Alert on repeated failures
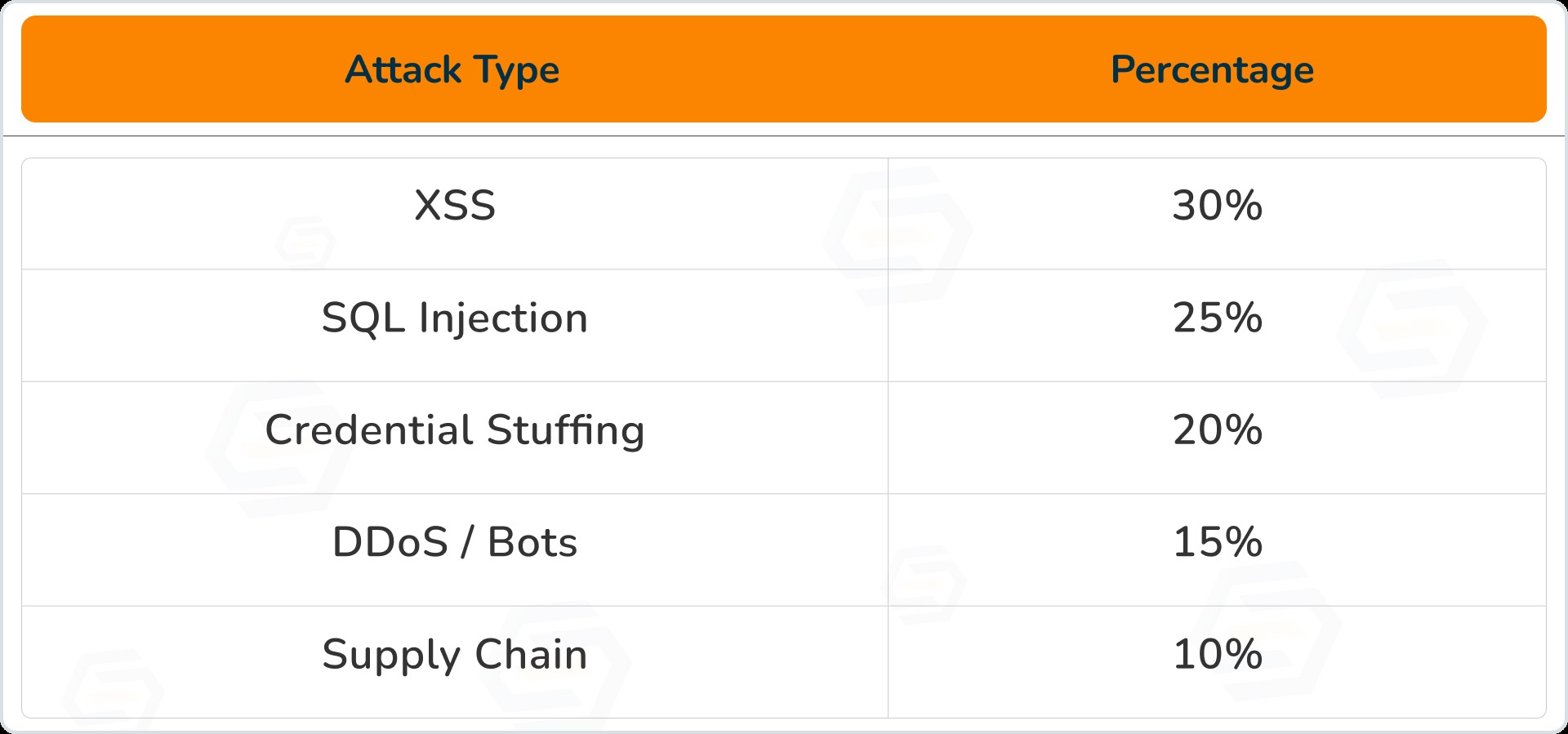
2026 Attack Types
Final Thoughts
-
Audit dependencies every week
-
Move to passkeys and OAuth
- Validate all inputs
- Secure secrets properly
-
Enforce HTTPS and TLS 1.3
-
Add rate limiting and WAF
-
Monitor logs actively
-
Over 55% of incidents come from dependencies
-
Passwords cause most credential breaches
- TLS 1.3 and rate limiting reduce attacks by up to 45%
- Continuous monitoring cuts detection time by 60%
Secure Your Node.js Stack with us
What we offer:
-
Complete Node.js security audits
-
Dependency and supply chain checks
- Modern authentication setup
- API security and WAF integration
-
Cloud and container security
-
Central logging and monitoring
-
Lower risk
-
Faster compliance
- Stronger customer trust



Vaishali Gaudani
Skilled React.js Developer with 3+ years of experience in creating dynamic, scalable, and user-friendly web applications. Dedicated to delivering high-quality solutions through innovative thinking and technical expertise.
Reply